COL believes that it is often necessary to look at the bigger picture, for example downtime caused from unauthorized people getting into your network and increasing productivity/flexibility/effectiveness/profitability by allowing secure remote access to your network by authorized employees away from the office. It is necessary to prevent unauthorized access to our clients network while at the same time authenticate the identity of authorized users and computers to maintain an appropriate level of network service operations and optimal network performance.
COL Provides Network Security addressing five main security objectives:
- Denies Access – Prevent unauthorized entry.
- Authentication - Proving identity to gain access.
- Integrity - Ensuring only authorized personnel can amend data.
- Confidentiality - Restricting data access.
- Non-repudiation- Decisive tracking of actions to a specific user
Benefits of COL Network Security:
Stop Hackers / Unauthorized Entry: Stop security breaches before they happen or, at worst, quarantine attacks in order to minimize disruption.
Increased Productivity: Limit or eliminate access to non-critical resources addressing potential security issues and improving productivity.
Improved Visibility and Control: Know who is connecting to the network, how they are connected and what they are accessing.
Legislative Compliance: Deploy security procedures and solutions to address the legalities associated with use of e-mail and the Internet.
Control and Management: Set strategic levels of security ensuring that the right people have the right level of access at any one time, and have the ability to amend this instantly, for example when people leave the organization.
Better Use of IT Resources: Monitor and manage spam and unauthorized web browsing ensuring adequate bandwidth for mission-critical applications.
Data Protection: Control the flow and content of data in and out of the organization protecting client, supplier and organizational confidentiality.
Types of Network Security Supported by COL:
Authentication
Controlling who has access to what data is a central theme of information security. Security built around passwords is too easy to defeat. User authentication becomes even more important when the user is remote. Whether users are dialing in from home into a Remote Access Server (RAS) solution or using a VPN connection these links provide the single most vulnerable link into a network. If an electronic identity can be faked the connection will provide an open path in the system.
Strong authentication addresses any of the vulnerabilities of single authentication. Furthermore, this stops an authorized user accidentally accessing another user's resource and allows that administrator to track all events linked to each individual user where necessary. Strong authentication can be achieved by incorporating more than one means of authentication: Something you have. Something you know. Something you are.
IDS – Intrusion Detection system
Intrusion Detection Systems are designed to alert system managers to potential trouble whether it is from an internal or external source. Commonly attackers make a tentative probe first, wait to see if it is detected and then home in on a subsequent attempt. IDS is an intelligent system that reads and interprets the contents of log files from routers, firewalls, servers and other network devices to identify the type of traffic on the network and network activity patterns. The IDS responds to alerts by raising an alarm, activating an automatic response action to limit potential damage and attempts to identify the intruder and correlate evidence of activity.
The main types of IDS:
· Network-based - looks for attack signatures and monitor network backbones
· Host-based - defends and monitors the operating and file systems.
· Application-based - monitors only specific applications
· Signature –based - looks for patterns in events specific to known attacks
· Anomaly-based - looks for anomalies in network activities that may indicate attacks
Firewall
A perimeter security measure permitting only authorized LAN access to and from the Internet. Access can be administered according to job description and user requirements rather than a 'one rule suits all' basis. The firewall analyses the traffic routed between the network and the Internet, both inbound and outbound, against set access criteria. Non-compliant traffic is stopped. Firewalls fall into four categories: packet filters, circuit level gateways, application level gateways and state full multilayer inspection firewalls.
Application Gateways (Proxies)
The first firewalls were application gateways, and are sometimes known as proxy gateways. These are made up of bastion hosts that run special software to act as a proxy server. This software runs at the Application Layer of our old friend the ISO/OSI Reference Model, hence the name. Clients behind the firewall must be proxitized (that is, must know how to use the proxy, and be configured to do so) in order to use Internet services. Traditionally, these have been the most secure, because they don't allow anything to pass by default, but need to have the programs written and turned on in order to begin passing traffic.
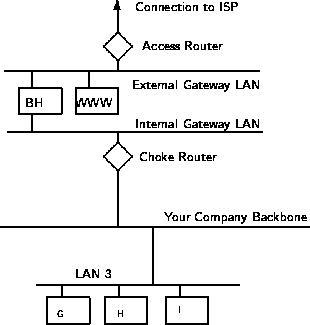
Packet Filters
Packet filtering is a technique whereby routers have ACLs (Access Control Lists) turned on. By default, a router will pass all traffic sent it, and will do so without any sort of restrictions. Employing ACLs is a method for enforcing your security policy with regard to what sorts of access you allow the outside world to have to your internal network, and vice versa.
Circuit Level Gateways
Operating at the session layer of the OSI. TCP handshaking between packets is analyzed to determine the legitimacy of requested sessions. Packets are not filtered by circuit level gateways.
State full Multilayer Inspection
A combination of the above firewalls. Packets are filtered at the network layer to determine whether session packets are legitimate and contents of packets are analyzed at the Application layer. Algorithms identify and process application layer data as opposed to application specific proxies.