Virtual Private Networks allow you to use the public internet to securely connect remote offices and remote employees at a fraction of the cost of dedicated, private telephone lines etc. There are two major uses for VPNs. The first is to connect two or more geographically separated networks, such as those at a main office and remote branch office. The second is to allow employees or authorized users to access a network from a remote PC. Both of these uses permit access to protected network resources by authorized users.
COL Ensure the VPN Security
To ensure the most secured service COL implement following types of security:
VPN Security: IPSec
Internet Protocol Security Protocol (IPSec) provides enhanced security features such as better encryption algorithms and more comprehensive authentication.
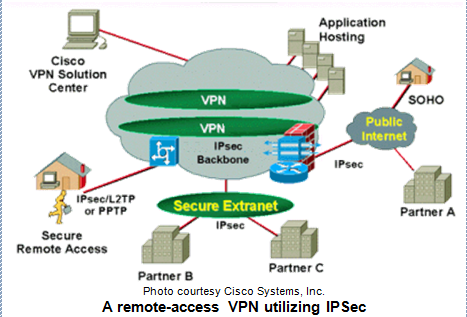
IPSec has two encryption modes: tunnel and transport. Tunnel encrypts the header and the payload of each packet while transport only encrypts the payload. Only systems that are IPSec compliant can take advantage of this protocol. Also, all devices must use a common key and the firewalls of each network must have very similar security policies set up. IPSec can encrypt data between various devices, such as:
- Router to router
- Firewall to router
- PC to router
- PC to server
VPN Security: Encryption
Encryption is the process of taking all the data that one computer is sending to another and encoding it into a form that only the other computer will be able to decode. Most
computer encryption systems belong in one of two categories:
- Symmetric-key encryption
- Public-key encryption
VPN Security: AAA Servers
AAA (authentication, authorization and accounting) servers are used for more secure access in a remote-access VPN environment. When a request to establish a session comes in from a dial-up client, the request is proxied to the AAA server. AAA then checks the following:
- Who you are (authentication)
- What you are allowed to do (authorization)
- What you actually do (accounting)
The accounting information is especially useful for tracking client use for security auditing, billing or reporting purposes.